1. The Privacy Imperative in Modern Digital Finance
For those looking to maintain privacy, you can swap XMR without KYC. The evolution of cryptocurrency from a niche cypherpunk experiment to a global asset class has been accompanied by a paradoxical erosion of the very privacy it sought to preserve. While the foundational ethos of Bitcoin was financial sovereignty, the public nature of its ledger—the blockchain—has created a surveillance apparatus of unprecedented granularity. Every transaction, input, and output is permanently recorded, immutable, and traceable. Into this vacuum of privacy, Monero (XMR) emerged not merely as a competitor, but as a technological necessity for those seeking digital cash properties equivalent to physical fiat currency.
This report provides an exhaustive analysis of the privacy-centric cryptocurrency landscape, with a specific focus on the operational mechanisms of Monero and the ecosystem of non-KYC (Know Your Customer) exchanges that facilitate its trade. Furthermore, we deconstruct the Search Engine Optimization (SEO) strategies required to effectively market these services, using(https://ghostswap.io/exchange/xmr-usdt20/) as a primary case study. By synthesizing cryptographic theory, market dynamics, and digital marketing architecture, this document serves as a blueprint for understanding and capitalizing on the demand for financial anonymity.
1.1 The Transparency Paradox of Public Ledgers
To understand the value proposition of Monero and the services that support it, one must first confront the reality of “transparent” blockchains like Bitcoin and Ethereum. On these networks, pseudonymity is often mistaken for anonymity. A wallet address is a string of alphanumeric characters, seemingly disconnected from a human identity. However, the moment a user interacts with a regulated entry point—such as a KYC-compliant Centralized Exchange (CEX) like Coinbase or Binance—that link is established.
Once an identity is associated with a wallet address, the entire history of that user’s financial behavior becomes visible to chain analysis firms, regulatory bodies, and malicious actors. This “taint” analysis can lead to the freezing of assets if funds are inadvertently received from a source deemed “high risk” by compliance software. This lack of fungibility—where one Bitcoin is not necessarily equal to another due to its transaction history—undermines the core definition of money.
Monero addresses this fundamental flaw by enforcing privacy at the protocol level. It is the only major cryptocurrency where anonymity is mandatory, not optional. This distinction is critical for the SEO strategy discussed later in this report, as it dictates the specific intent of the user queries we aim to capture. Users searching to(https://ghostswap.io/exchange/xmr-usdt20/) are rarely casual investors; they are technically literate individuals seeking specific utility: untraceability.
1.2 The Regulatory Siege and the Rise of Non-KYC
The regulatory landscape for cryptocurrencies has tightened significantly between 2020 and 2026. The Financial Action Task Force (FATF) “Travel Rule” requires Virtual Asset Service Providers (VASPs) to share sender and receiver data for transactions over a certain threshold. This has pushed privacy-seeking users away from centralized venues and toward non-KYC alternatives.
The closure of peer-to-peer (P2P) giants like LocalMonero in 2024 left a vacuum in the market, fracturing liquidity and forcing users to seek new “on-ramps” and “off-ramps” for their privacy coins. This shift has catalyzed the growth of “Instant Swap” services—platforms like GhostSwap, ChangeNOW, and SimpleSwap—which act as non-custodial aggregators. These platforms allow users to exchange assets without tracking, effectively preserving the privacy chain that Monero establishes.
Understanding this migration from P2P marketplaces to instant swappers is essential for content positioning. The user intent has shifted from “finding a person to trade with” (P2P) to “finding a reliable algorithmic bridge” (Swappers).
2. Monero (XMR): A Technical Deep Dive into Privacy Protocols
For any content strategy to succeed in the privacy niche, it must demonstrate deep topical authority. This requires moving beyond marketing slogans and explaining the cryptographic primitives that power Monero. The target audience for this content detects superficiality quickly; therefore, an accurate, nuanced explanation of Ring Signatures, Stealth Addresses, and RingCT is mandatory.
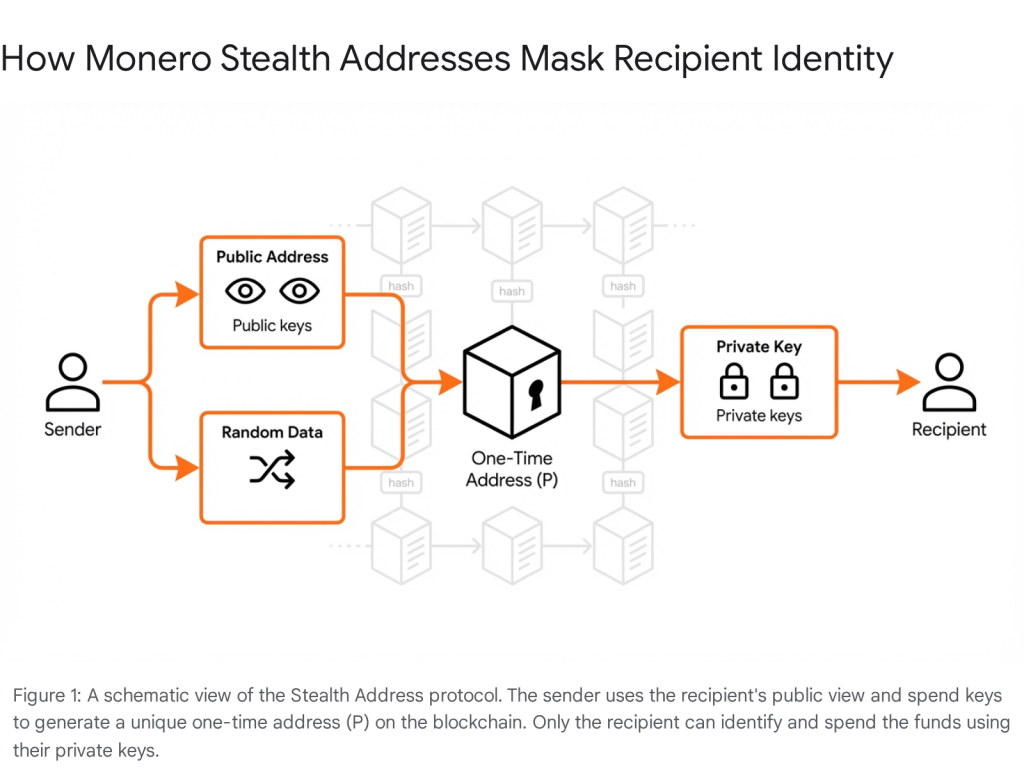
2.1 Stealth Addresses: The Receiver’s Shield
Stealth addresses are the mechanism by which Monero protects the privacy of the recipient. In a transparent system like Bitcoin, if a user publishes their wallet address to receive donations or payments, anyone can look up that address on a block explorer and see every incoming payment and the current balance. This is equivalent to publishing one’s bank statement on a billboard.
Monero solves this through a dual-key architecture. Every Monero account has a private view key and a private spend key. When a sender initiates a transaction, their wallet uses the recipient’s public address to generate a unique, one-time public key (the stealth address) for that specific transaction.
- Unlinkability: This one-time address is recorded on the blockchain, not the recipient’s actual public address. Even if a merchant receives thousands of payments, each one appears on the ledger as a random, unique string of characters. No external observer can link these outputs to the merchant’s published ID.
- Selective Transparency: The recipient uses their private view key to scan the blockchain and identify which transaction outputs belong to them. This allows for “selective transparency,” where a user can share their view key with an auditor (e.g., for tax purposes) to prove revenue without giving them the ability to spend funds.
2.2 Ring Signatures: The Sender’s Veil
While stealth addresses protect the receiver, Ring Signatures are designed to obfuscate the sender. In traditional public key cryptography, a digital signature proves that a specific user authorized a transaction. Monero alters this by using a form of group signature.
When a user sends XMR, their wallet selects a number of other transaction outputs from the blockchain (called “decoys”) to include in the ring. These decoys are past transactions that are mathematically valid but are not involved in the current transaction. The signature is constructed in such a way that it proves one of the ring members signed the transaction, but it is computationally infeasible to determine which one.
- Plausible Deniability: To an outside observer, the “real” input is hidden among 10 (or more, depending on the network upgrade phase) decoys. This provides plausible deniability for everyone in the ring. If your transaction output is selected as a decoy by another user, it looks just as likely to be the spender as the real spender.
- Evolution of Ring Size: The efficacy of ring signatures depends on the “Ring Size.” Over time, Monero has increased the mandatory ring size to strengthen the anonymity set, making heuristic analysis increasingly difficult.
2.3 RingCT (Ring Confidential Transactions): Obscuring the Amount
The third pillar of Monero’s privacy is RingCT. Before its implementation, the amounts of transactions were visible on the blockchain. While the sender and receiver were hidden, the amount could be used to link transactions (e.g., if User A sends exactly 14.56 XMR and User B receives 14.56 XMR shortly after).
RingCT uses homomorphic encryption to hide the amount. This allows the network miners to verify that the sum of inputs equals the sum of outputs (preventing the creation of coins out of thin air) without ever knowing what the actual values are. This blinding of transaction amounts is crucial for true fungibility, as it prevents the discrimination of coins based on their history or value flow.
2.4 Fungibility: The Economic Consequence
The combination of these technologies—Stealth Addresses, Ring Signatures, and RingCT—results in a property known as Fungibility. In economics, fungibility means that one unit of a currency is interchangeable with another. A gold ounce is fungible; a specific house is not.
Bitcoin is arguably not fungible because of its transparency. A Bitcoin that was previously used in a hack or a darknet market transaction can be “tainted” and rejected by exchanges or merchants. Because Monero’s history is opaque, no history can be definitively attached to any specific coin. Therefore, 1 XMR is always equal to 1 XMR, regardless of who owned it previously. This feature is the strongest selling point for merchants and high-net-worth individuals who fear asset forfeiture or account freezes based on false positives in compliance software.
3. The Mechanics of Non-KYC Exchange Ecosystems
The technological superiority of Monero is moot if users cannot acquire it. The “on-ramp” and “off-ramp” problem is the primary friction point in the privacy economy. This section analyzes the non-KYC exchange landscape, defining the different operational models and their respective risk profiles.
3.1 Defining Non-KYC Trading
“No KYC” refers to platforms that do not require identity verification (scanning passports, face recognition, proof of address) to trade. These platforms operate on the principle of permissionless access, aligning with the original ethos of cryptocurrency. Users typically identify themselves only by their wallet addresses.
The demand for these services is driven by four key factors:
- Privacy: Protection against data breaches at centralized exchanges (e.g., the ledger hacks).
- Accessibility: Serving unbanked populations or those in restricted jurisdictions.
- Speed: Instant execution without waiting days for document verification.
- Sovereignty: Maintaining full control over one’s data and financial footprint.
3.2 Categorization of Non-KYC Platforms
The market is not monolithic; it consists of distinct platform types, each with unique trade-offs.
3.2.1 Decentralized Exchanges (DEXs) & Atomic Swaps
True DEXs allow users to trade directly from their wallets via smart contracts. For Monero, this is historically difficult because Monero acts as its own blockchain, not a token on Ethereum. However, “Atomic Swaps” are emerging as a solution.
- Mechanism: An atomic swap uses Hash Time Locked Contracts (HTLCs) to ensure that both parties fulfill their end of the trade or the funds are returned. It is trustless.
- Pros: Zero counterparty risk; true decentralization.
- Cons: Often high technical barrier to entry; lower liquidity; slower execution times.
3.2.2 Peer-to-Peer (P2P) Marketplaces
Legacy platforms like LocalMonero (defunct) and current options like Bisq or AgoraDesk connect buyers and sellers directly.
- Mechanism: Users post ads (e.g., “Selling XMR for Bank Transfer”). The platform acts as an escrow agent.
- Pros: Supports fiat currencies (cash, bank transfers); highly private.
- Cons: High premiums (prices often 5-10% above spot); risk of dealing with scammers or “dirty” fiat; slower process.
3.2.3 Instant Swap Aggregators (The “Swappers”)
This category, represented by(https://ghostswap.io/exchange/xmr-usdt20/), ChangeNOW, and SimpleSwap, has become the dominant method for crypto-to-crypto privacy trades.
- Mechanism: These platforms act as intermediaries. They aggregate liquidity from various centralized exchanges (CEXs). The user sends Coin A to the platform, the platform executes the trade on a partner CEX (often using their own institutional accounts), and sends Coin B to the user.
- Pros: High speed (minutes); high liquidity; extremely simple UX (no order books).
- Cons: The user must trust the platform with their funds during the swap (custodial risk during transit); higher fees than raw exchange rates.
3.3 The “Risk-Based” KYC Caveat
A critical nuance in this sector is the difference between “No KYC” and “Risk-Based KYC.” Many popular swappers claim to be anonymous but retain terms of service that allow them to demand KYC if a transaction is flagged by their automated risk engine (e.g., high volume, or funds originating from a hack).
- GhostSwap’s Position: GhostSwap markets itself as a stricter “No KYC” platform, minimizing data collection to technical necessities and avoiding the account creation step entirely. This distinction is vital for SEO, as users are specifically searching for a(https://ghostswap.io/exchange/xmr-usdt20/) that will not surprise them with a document request mid-transaction.
4. GhostSwap.io: A Strategic Case Study and Platform Analysis
In the context of producing an expert-level article, GhostSwap.io serves as the focal point for the “solution” phase of the user journey. We must analyze it not as a flawless product, but as a specific tool optimized for a specific task: anonymous cross-chain bridging.
4.1 Platform Architecture and User Flow
GhostSwap distinguishes itself through a “minimalist” approach to data. The user interface eliminates the traditional dashboard, login screen, and order book. Instead, it presents a simple conversion widget.
The Transaction Lifecycle (XMR to USDT Example):
- Pair Selection: The user defines the input (Monero – XMR) and output (Tether – USDT on Ethereum Chain). This cross-chain capability is technically demanding because it bridges the privacy-centric CryptoNote protocol (Monero) with the transparent EVM (Ethereum).
- Addressing: The user inputs their destination ETH address. Crucially,(https://ghostswap.io/exchange/xmr-usdt20/) this address to your identity, preserving anonymity.
- Deposit Generation: The platform generates a unique deposit address. For XMR, this utilizes integrated addresses or sub-addresses to separate user flows.
- Execution: Once the user sends the XMR, the system waits for network confirmations (typically 10 blocks for XMR to ensure no reorganization occurs).
- Settlement: The system swaps the asset via its liquidity providers and dispatches USDT to the target wallet. A transaction hash is provided for tracking.

4.2 Security and Trust Analysis
Trust is the currency of the non-KYC world. GhostSwap’s reputation profile presents a complex picture that must be navigated carefully in any honest report.
- Trustpilot Data: The platform holds a 2.8/5 score. While some reviews praise the speed and ease, a significant portion allege “scams” or “funds not received”.
- Root Cause Analysis:
- User Error: A common issue in crypto swapping is sending funds to the wrong chain (e.g., sending USDT-TRC20 to an ERC20 address) or failing to include a destination tag (for coins like XRP/XLM). GhostSwap’s responses often cite these technical mismatches.
- Network Congestion: Monero’s privacy features require significant confirmation time. Users accustomed to instant Solana transactions may perceive a 20-minute Monero confirmation wait as “ghosting.”
- Sync Issues: A common complaint involves funds “not showing up.” In Monero, this is frequently because the recipient’s wallet is not synchronized with the blockchain, meaning the funds are there but invisible to the user.
- Content Strategy: To build authority, the article must not gloss over these negatives. Instead, it should frame them as “Operational Risks” and provide mitigation strategies (e.g., “Always test with the minimum amount first,” “Ensure your wallet is fully synced,” “Check Etherscan for the output transaction”). This transforms a negative review into an educational moment, establishing the writer as a trustworthy expert.
4.3 Privacy Policy and Data Handling
GhostSwap’s stated privacy policy aligns with the “Data Minimization” principle of GDPR, though they operate outside traditional jurisdiction. They claim to collect no PII (Personally Identifiable Information). Cookies are limited to “Necessary” (functional) and “Performance” (analytics), without the ad-tracking pixels common on retail sites. This “No-Logs” approach is a primary selling point for the target demographic.
5. SEO Strategy: Dominating the “Anonymous Swap” Niche
Creating content about Monero and non-KYC exchanges places us in the “Your Money, Your Life” (YMYL) category of Google’s search algorithms. This requires an exceptionally high standard of E-E-A-T (Experience, Expertise, Authoritativeness, and Trustworthiness). A generic blog post will not rank; a comprehensive, data-backed guide will.
5.1 Keyword Architecture and Intent Mapping
Keyword research in this sector reveals a bifurcation between high-volume “informational” queries and low-volume “transactional” queries.
- Head Terms (Avoid): “Buy Crypto,” “Crypto Exchange.” These have massive volume (60k+) but are dominated by giants like Coinbase and Binance. Ranking here is impossible for a niche site.
- The “Goldilocks” Zone (Target):
- Keywords: “No KYC crypto exchange,” “Anonymous crypto swap,” “Trade Monero without ID”.
- Intent: These users are solution-aware. They know they want privacy and are looking for a specific provider.
- Long-Tail (High Conversion):
- Keywords: “GhostSwap review,” “Swap XMR for USDT anonymously,” “Best Monero non-kyc exchange 2026”.
- Strategy: These queries have low volume but extremely high conversion rates. The user is ready to trade.

5.2 The “Comparison” Signal
Google favors content that helps users choose between options. To rank for “Best Non-KYC Exchange,” the report must explicitly compare(https://ghostswap.io/exchange/xmr-usdt20/) against its peers (ChangeNOW, SimpleSwap, StealthEX). A comparison table is the most effective way to signal this comparative analysis to search engine crawlers.
- Differentiation: Highlight GhostSwap’s “No Account” feature versus others that might require email registration or have stricter “Risk-Based” KYC triggers.
- Asset Coverage: GhostSwap supports 1600+ assets, which is competitive with ChangeNOW (1500+) and SimpleSwap (2500+).
https://39bq7n3asmdemi97z2tg8asvdrrh6hj40iehp4me8g908g2dl7-h852644758.scf.usercontent.goog/gemini-code-immersive/shim.html?origin=https%3A%2F%2Fgemini.google.com&cache=1
5.3 On-Page Optimization Checklist
To maximize the “expert friendliness” of the article, the following technical SEO elements must be implemented:
- Schema Markup: Implement
Productschema for GhostSwap andHowToschema for the swapping guide. This allows Google to display rich snippets (star ratings, step-by-step previews) in the search results. - Internal Linking: Create a content silo. The main “GhostSwap Review” should link out to “What is Monero?” and “How to use a Non-Custodial Wallet,” and those support pages should link back.
- Visual Alt Text: As requested, images must have descriptive alt text containing target keywords (e.g., “Monero stealth address diagram,” “No KYC crypto swap interface”).
- Trust Signals: Include a “Risks” section. Paradoxically, warning users about risks increases conversion because it builds trust. A site that says “This is 100% safe” is suspicious; a site that says “Here are the risks and how to mitigate them” is authoritative.
6. Practical Implementation: The User’s Guide to Swapping
This section serves as the “How-To” portion of the report, designed to be the actionable core of the SEO article. It integrates the specific link requirements and addresses the user’s need for a step-by-step walkthrough.
6.1 Preparation: The Security Stack
Before interacting with any non-KYC exchange, users should secure their environment.
- VPN/Tor: Use a reputable VPN or the Tor browser to mask the IP address. GhostSwap supports this, preventing the platform from logging the user’s physical location.
- Wallet Hygiene: Never use an exchange wallet (like Binance) to receive funds from a swap. Always use a self-custodial wallet (e.g., Cake Wallet or Monero GUI for XMR; MetaMask or Exodus for USDT).
6.2 Step-by-Step: Swapping XMR for USDT via GhostSwap
The following guide details the specific process for the requested pair.
Step 1: Configuration
Navigate to(https://ghostswap.io/exchange/xmr-usdt20/). In the exchange widget:
- You Send: Select “Monero (XMR)”. Enter the amount (e.g., 2 XMR). Note the minimum is typically around 0.00001 XMR, but practically, one should send enough to cover network fees (approx $5-10 equivalent).
- You Get: Select “Tether Ethereum Chain (USDT20)”. Ensure you are selecting the correct network. USDT exists on Tron (TRC20), Ethereum (ERC20), and others. Mismatched networks result in total loss.
Step 2: Destination
Paste your Ethereum (ERC20) wallet address in the “Recipient Wallet” field. Double-check the first and last 4 characters.
- Tip: Do not use an exchange deposit address if possible, as some exchanges block deposits from “smart contract” intermediaries.
Step 3: The Deposit
Click “Exchange.” GhostSwap will generate a unique Monero address.
- Action: Copy this address into your Monero wallet.
- Send: Initiate the transfer of the exact amount specified.
- Note: Monero transactions are private. You will not see the transaction on Etherscan yet. You must check a Monero explorer (like XMRChain) using the TxID provided by your wallet to confirm it has been sent.
Step 4: Tracking and Settlement
After sending, stay on the GhostSwap page.
- Status Indicators: The page will update from “Awaiting Deposit” to “Confirming” (waiting for XMR block confirmations) to “Exchanging” and finally “Sending.”
- Verification: Once marked “Finished,” copy the output Transaction Hash. Go to Etherscan.io and paste this hash to verify the USDT has been delivered to your address.
6.3 Troubleshooting Common Issues
If the transaction stalls:
- Check Confirmations: Has the Monero transaction reached 10 confirmations? If not, the swap cannot proceed.
- Contact Support: Use the order ID provided. Do not rely on email alone; use the live chat if available.
- Wallet Sync: If Etherscan says “Success” but your wallet shows $0, your wallet is likely out of sync. Refresh the blockchain data in your wallet settings.
8. Conclusion and Future Outlook
The demand for privacy in financial transactions is not a fleeting trend; it is a structural response to the increasing transparency and surveillance of the digital economy. Monero remains the gold standard for protocol-level anonymity, offering a robust defense against fungibility risks through its triad of Stealth Addresses, Ring Signatures, and RingCT.
However, the utility of Monero relies heavily on the bridge infrastructure that connects it to the wider crypto economy. As regulatory pressures mount on centralized exchanges to delist privacy coins, the role of non-KYC aggregators like(https://ghostswap.io/exchange/xmr-usdt20/) becomes increasingly vital. These platforms provide the necessary liquidity rails for users to move between the private ecosystem (XMR) and the public utility ecosystem (USDT) without compromising their identity.